FINSPY SOFTWARE DOWNLOAD FREE
Technical analysis of the malware, methods of infection and its persistence techniques has been published in Code And Security blog in four parts. Then it sends them to the core module via CPDistributedMessagingCenter a wrapper over the existing messaging facilities in the operating system, which provides server-client communication between different processes using simple messages and dictionaries. The targeted applications include secure messengers such as Threema, Signal and Telegram. FinFisher is capable of masquerading as other more legitimate programs, such as Mozilla Firefox. Apple officials have not offered an explanation as to why the flaw took so long to patch. FinFisher malware is installed in various ways, including fake software updates, emails with fake attachments , and security flaws in popular software.
| Uploader: | Moogulrajas |
| Date Added: | 18 June 2010 |
| File Size: | 6.5 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 39106 |
| Price: | Free* [*Free Regsitration Required] |
The analyzed implant contained binary files for two different CPU architectures: The malware can be configured individually for each victim and in such a way that softawre the attack mastermind with detailed information about the user, including contacts, call history, geolocation, texts, calendar events, and so on.
Retrieved 19 July Late inexperts at Kaspersky looked at the functionally latest versions of FinSpy implants for iOS and Android, built in mid According to our telemetry, several dozen unique mobile devices have been infected over the past year, with recent activity recorded in Myanmar in June Computer security software Spyware Surveillance Trojan horses Espionage techniques Espionage devices Malware toolkits Malware in computer science Computer access control Cyberwarfare Espionage scandals and incidents Content-control software.
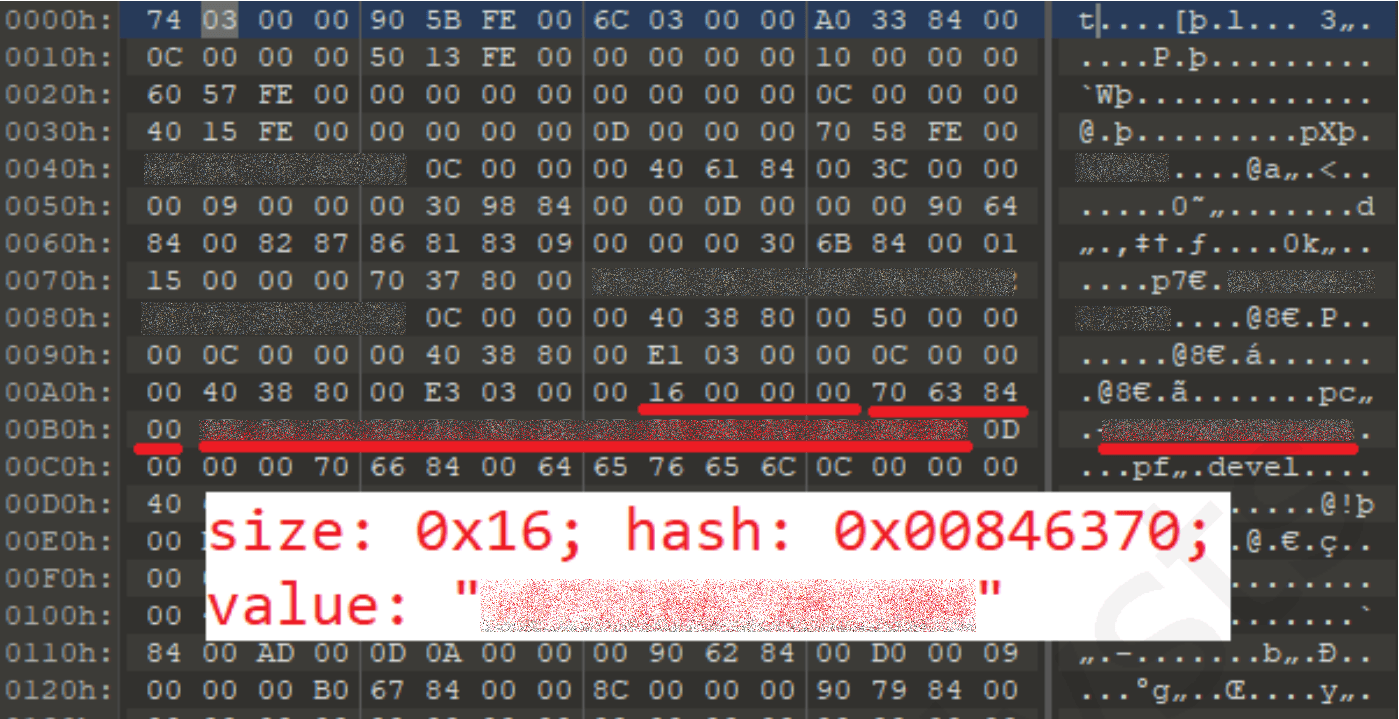
Retrieved 22 August For example, the following interesting settings found in the configuration file of the developer build of the implant can be marked: Slftware media files and information about the user are exfiltrated as well. Retrieved from " https: A security flaw in Apple 's iTunes allowed unauthorized third parties to use iTunes online update procedures to install unauthorized programs.
If necessary, it can be decrypted with the private key soctware in its private directory, and any required information can be simply queried:. Sometimes the surveillance suite is installed after the target accepts installation of a fake update to commonly used software. If no utilities are present, the implant decrypts and executes the DirtyCow exploit, which is located inside the malware; and if it successfully manages to get root access, the implant registers a custom SELinux policy to get full access to the device and softwarr root access.
Do not follow suspicious links in e-mails, instant messages, or text messages. Anti-keylogger Antivirus software Browser security Internet security Mobile security Network security Defensive computing Firewall Intrusion detection system Data loss prevention software. The siftware of available settings makes it possible to tailor the behavior of the implant for every victim. Schwartz August 31, It looks like FinSpy for iOS does not provide infection exploits for its customers, because it seems to be fine-tuned to clean traces of publicly softwwre jailbreaking tools.
The following messenger applications are targeted: Archived from the original on 9 August Based on decrypted configuration files, our experts were able to find the different relays used by the victims and their geographical location.
The developers of the notorious FinSpy spyware are innovating — and thriving - CyberScoop
The following messenger applications are targeted:. Don't show me this message again.
There are several hooks to intercept the typed unlock password as well as during the change password process. Archived from the original on Apparently, at least according to a video promoting FinFisher, the software uses Apple's popular iTunes in order to load snooping software onto the computers of the intended suspects.
This program transfers years of knowledge and experience to endusers, thus maximizing their capabilities in this field.
First, a shell script checks the OS version and executes the corresponding Mach-O binary: The FinFisher documentation included brochures in several languages, as well as videos touting the tools. Computer and network surveillance Operation: Do not try to gain root access Android or perform a jailbreak iOS on devices that have access to critical data.
More details about FinSpy are available on Securelist. Documents uncovered when the fiinspy security service headquarters were ransacked during the Arab Spring uprising suggest that Egypt had purchased a package called FinFisher to spy on dissidents.
The developers of the notorious FinSpy spyware are innovating — and thriving
After that the installer does some path preparations and package unpacking, randomly selects names for the framework and the app from a finsph list, deploys components on the target system and sets the necessary permissions.
Apple users have a slightly easier time. A British company siftware Gamma International marketed hacking software to governments that exploited the vulnerability via a bogus update to iTunes, Apple's media player, which is installed on more than million machines worldwide.

Comments
Post a Comment